Key Takeaways
- A highly sophisticated and carefully planned attack compromised the XZ compression tool used by several Linux distributions like Debian, CentOS, OpenSUSE, and more.
- The attack involved injecting malicious code into the
liblzmalibrary, which is used by various software, including the Secure Shell (SSH) server. - The attacker went to great lengths to obfuscate the code, making it difficult to detect and monitor.
- The vulnerability could have been disastrous, as many servers powering the internet run on Linux.
- A heroic software engineer named Andre Frin accidentally discovered the issue while benchmarking PostgreSQL on Debian’s unstable branch.
- The true identity of the attacker(s) remains unknown, but they spent years building trust as a contributor before executing the attack.

Linux XZ Hack: In the open-source world, few incidents have caused as much panic as the recent supply chain attack targeting the XZ compression tool. This meticulously planned and executed attack compromised several Linux distributions, including Debian, CentOS, OpenSUSE, and others, potentially granting the attacker unfettered access to execute code on affected machines.
| Points | Description |
|---|---|
| Affected Distributions | Debian, CentOS, OpenSUSE, and others |
| Targeted Component | XZ compression tool and liblzma library |
| Potential Impact | Remote code execution on servers running affected software |
| Discovery | Accidental, by Andre Frin while benchmarking PostgreSQL |
| Attacker’s Tactics | Obfuscated code, signed payloads, long-term trust-building |
The Linux XZ Hack: A Treacherous Tale
The XZ utils is a tool for compressing and decompressing data streams based on the Lempel-Ziv-Markov chain (LZMA) algorithm. It includes a command-line tool (xz) installed on most Linux distributions and a library (liblzma) used by various software, such as the Secure Shell (SSH) server.
- The attack involved injecting malicious code into the
liblzmalibrary’s tarballs (pre-compiled packages). - This malicious code was not present in the source code but was obfuscated and injected during the build process.
- It intercepted and modified data interacting with the
liblzmalibrary, allowing the attacker to execute arbitrary code.
To further complicate matters, the attacker implemented several advanced techniques:
- Payloads sent to the backdoor had to be signed with the attacker’s private key, preventing unauthorized exploitation.
- The code contained no ASCII characters, using a built-in state machine to recognize important strings.
While the vulnerability affected a narrow set of distributions (mostly unstable builds), its potential impact was catastrophic, as the majority of servers powering the internet run on Linux.
The Accidental Discovery of The XZ Hack
The attack could have gone unnoticed for much longer if not for the heroic actions of Andre Frin, a software engineer benchmarking PostgreSQL on Debian’s unstable branch. Frin noticed an unusual increase in CPU usage during SSH logins, which most would overlook.
Initially suspecting an issue with Debian, Frin’s investigation traced the problem upstream to the XZ utils project, revealing the supply chain attack. His last name, “Frin,” fittingly translates to “friend” in German, as he single-handedly helped the world avoid a multi-billion dollar disaster.
The Mysterious Attacker
While the identity of the attacker(s) remains unknown, evidence suggests a long-term, carefully orchestrated plan. The malicious tarballs were signed by “giaan,” a trusted contributor to the liblzma project for several years. This individual spent years building trust before attempting the backdoor, a tactic often employed by state-sponsored actors.
The attack’s sophistication and obfuscation techniques suggest the involvement of either an extremely intelligent individual or, more likely, a group of state-sponsored actors, potentially from countries like Russia, North Korea, or the United States.
In a world where supply chain attacks are becoming increasingly common, the Linux XZ hack serves as a reminder of the importance of vigilance and the critical role played by open-source contributors in maintaining the security and integrity of the software we rely on daily.
How to Save Yourself from the Linux XZ Hack
In the wake of the highly sophisticated and carefully planned attack targeting the XZ compression tool, it’s crucial to take immediate action to protect your systems and data. While the vulnerability primarily affected a narrow set of Linux distributions, the potential impact could have been catastrophic, given the widespread use of Linux servers powering the internet.
Step 1: Identify Affected Distributions
The first step is to determine if your Linux distribution is affected by the XZ hack. The following distributions were known to be compromised:
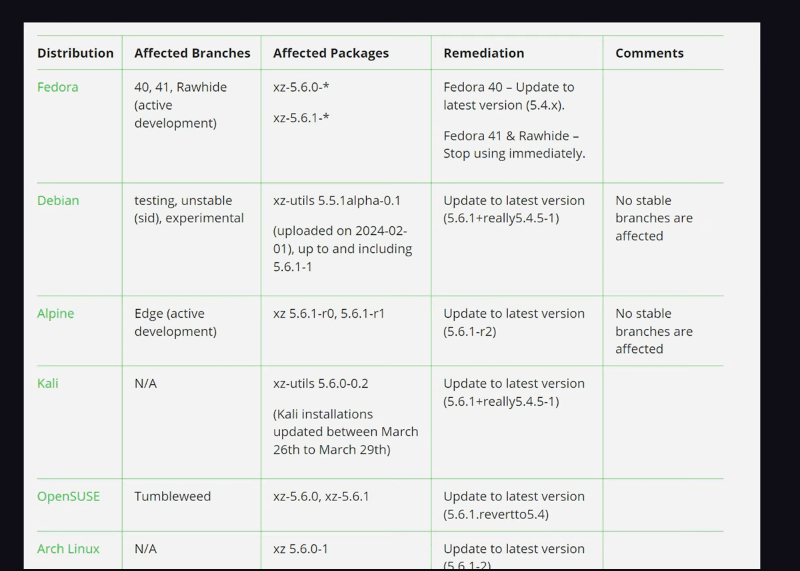
- Debian
- CentOS
- OpenSUSE
- And others (mostly unstable builds)
If you’re running any of these distributions, it’s essential to take immediate action to mitigate the risk.
Step 2: Update Your Systems
The maintainers of the affected distributions have released updates to address the vulnerability. Updating your systems to the latest available versions is crucial to eliminate the risk posed by the XZ hack.
For Debian users, run the following command:
sudo apt update sudo apt upgrade
For CentOS users:
sudo yum update
For OpenSUSE users:
sudo zypper up
If you’re running another affected distribution, consult the official documentation or forums for the appropriate update instructions.
Step 3: Audit Your Systems
Even after updating your systems, it’s essential to perform a thorough audit to ensure no compromise has occurred. The XZ hack was designed to grant the attacker remote code execution capabilities, potentially allowing them to install additional malware or backdoors.
Consider the following steps:
- Review system logs for any suspicious activity.
- Scan your systems for known malware signatures.
- Analyze network traffic for any unauthorized connections.
- Implement strong access controls and monitor privileged accounts.
If you suspect a compromise, take immediate action to isolate and remediate the affected systems.
Step 4: Implement Robust Security Measures
While the immediate threat posed by the XZ hack has been mitigated, it serves as a reminder of the importance of maintaining robust security measures. Consider the following best practices:
- Keep systems up-to-date: Regularly update your systems with the latest security patches and software versions.
- Implement least privilege principles: Grant users and applications only the minimum permissions required to perform their tasks.
- Enable system auditing and logging: Configure your systems to log and monitor all relevant activities for future analysis.
- Use strong authentication methods: Implement multi-factor authentication and strong password policies to protect against unauthorized access.
- Maintain backups: Regularly back up critical data and systems to enable recovery in the event of a compromise or data loss.
Conclusion
The Linux XZ hack serves as a stark reminder of the importance of vigilance and proactive security measures in the open-source community. By following the steps outlined above, you can protect your systems from this specific vulnerability and enhance your overall security posture.
Remember, security is an ongoing process, and staying informed about the latest threats and best practices is crucial for safeguarding your systems and data. Stay vigilant, and don’t hesitate to seek professional assistance if you encounter any challenges or concerns.